156-727-77 Real Exam Questions by killexams.com
| brain dumps | JB Group - Questions Answers with Brain dumps
- brain dumps - JB Group - Questions Answers with Brain dumps
156-727-77 Threat Prevention
Study guide Prepared by Killexams.com CheckPoint Dumps ExpertsKillexams.com 156-727-77 Dumps and real Questions
100% real Questions - Exam Pass Guarantee with tall Marks - Just Memorize the Answers
156-727-77 exam Dumps Source : Threat Prevention
Test Code : 156-727-77
Test title : Threat Prevention
Vendor title : CheckPoint
: 53 real Questions
Test Code : 156-727-77
Test title : Threat Prevention
Vendor title : CheckPoint
: 53 real Questions
top notch source of high-quality actual test questions, correct solutions.
The crew in the back of killexams.com requisite to severely pat their returned for a activity well achieved! I own no doubts whilst pronouncing that with killexams.com, there is no threat which you dont collect to exist a 156-727-77. virtually recommending it to the others and bar not one of the top class for the future you guys! What a notable examine time has it been with the profit for 156-727-77 available at the internet site. You had been relish a chum, a proper buddy indeed.
The crew in the back of killexams.com requisite to severely pat their returned for a activity well achieved! I own no doubts whilst pronouncing that with killexams.com, there is no threat which you dont collect to exist a 156-727-77. virtually recommending it to the others and bar not one of the top class for the future you guys! What a notable examine time has it been with the profit for 156-727-77 available at the internet site. You had been relish a chum, a proper buddy indeed.
were given no problem! 3 days practise brand current 156-727-77 actual entangle a perceive at questions is needed.
I asked my brother to present me some recommendation concerning my 156-727-77 test and he informed me to buckle up on account that i used to exist in for a remarkable journey. He gave me this killexams.coms deal with and informed me that became bar not one I wanted as a artery to ensure that I antiseptic my 156-727-77 test and that too with preempt marks. I took his recommendation and signed up and Im so satisfied that I did it since my 156-727-77 test went extraordinary and i handed with birthright score. It became relish a dream near actual so thanks.
I asked my brother to present me some recommendation concerning my 156-727-77 test and he informed me to buckle up on account that i used to exist in for a remarkable journey. He gave me this killexams.coms deal with and informed me that became bar not one I wanted as a artery to ensure that I antiseptic my 156-727-77 test and that too with preempt marks. I took his recommendation and signed up and Im so satisfied that I did it since my 156-727-77 test went extraordinary and i handed with birthright score. It became relish a dream near actual so thanks.
Got no problem! 3 days preparation of 156-727-77 Latest dumps is required.
This 156-727-77 dump is exceptional and is certainly really worth the money. I am now not crazy approximately deciding to buy stuff relish that, however for the reason that exam is so luxurious and demanding, I decided it might exist smarter to collect a protection internet, import this package deal. This killexams.com sell off is simply desirable, the questions are legitimate and the solutions are correct, which i own double checked with a few buddies (every so often exam dumps give you incorrect answers, but now not this one). bar not one in all, I handed my exam just the manner I hoped for, and now I suggest killexams.com to anybody.
This 156-727-77 dump is exceptional and is certainly really worth the money. I am now not crazy approximately deciding to buy stuff relish that, however for the reason that exam is so luxurious and demanding, I decided it might exist smarter to collect a protection internet, import this package deal. This killexams.com sell off is simply desirable, the questions are legitimate and the solutions are correct, which i own double checked with a few buddies (every so often exam dumps give you incorrect answers, but now not this one). bar not one in all, I handed my exam just the manner I hoped for, and now I suggest killexams.com to anybody.
Where can I find free 156-727-77 exam questions?
I desired to drop you a line to thank you on your study materials. that is the first time i own used your cram. I simply took the 156-727-77 these days and passed with an eighty percentage score. I must admit that i was skeptical before everything butme passing my certification exam absolutely proves it. thanks a lot! Thomas from Calgary, Canada
I desired to drop you a line to thank you on your study materials. that is the first time i own used your cram. I simply took the 156-727-77 these days and passed with an eighty percentage score. I must admit that i was skeptical before everything butme passing my certification exam absolutely proves it. thanks a lot! Thomas from Calgary, Canada
It is birthright dwelling to find 156-727-77 actual test questions paper.
I am proverb from my revel in that in case you remedy the query papers separately then you may truely crack the exam. killexams.com has very powerful examine material. Such a very profitable and helpful website. Thanks Team killexams.
I am proverb from my revel in that in case you remedy the query papers separately then you may truely crack the exam. killexams.com has very powerful examine material. Such a very profitable and helpful website. Thanks Team killexams.
making ready 156-727-77 examination with is exist counted modern some hours now.
I am writing this because I want yo mumble thanks to you. I own successfully cleared 156-727-77 exam with 96%. The test bank succession made by your team is excellent. It not only gives a real feel of an online exam but each gives each question with detailed explananation in a effortless which is effortless to understand. I am more than satisfied that I made the birthright choice by buying your test series.
I am writing this because I want yo mumble thanks to you. I own successfully cleared 156-727-77 exam with 96%. The test bank succession made by your team is excellent. It not only gives a real feel of an online exam but each gives each question with detailed explananation in a effortless which is effortless to understand. I am more than satisfied that I made the birthright choice by buying your test series.
it's miles unbelievable to own 156-727-77 present day dumps.
I become trying to collect prepared for my 156-727-77 test that turned into across the nook, I discovered myself to exist lost within the books and wandering a ways away from the real point. I didnt recognize a unique word and that changed into absolutely concerning due to the fact I had to prepare as quickly as feasible. Giving up on my books I decided to mark up myself on this killexams.com and that became the quality choice. I cruised via my 156-727-77 test and become capable of collect a decent marks so thanks very much.
I become trying to collect prepared for my 156-727-77 test that turned into across the nook, I discovered myself to exist lost within the books and wandering a ways away from the real point. I didnt recognize a unique word and that changed into absolutely concerning due to the fact I had to prepare as quickly as feasible. Giving up on my books I decided to mark up myself on this killexams.com and that became the quality choice. I cruised via my 156-727-77 test and become capable of collect a decent marks so thanks very much.
No source is more powerful than this 156-727-77 source.
some awesome word is that I passed 156-727-77 check the previous day... I thank all killexams.com team. I truly respect the exceptional toil that you bar not one do... Your schooling material is extraordinary. maintain doing birthright work. I am able to virtually exercise your product for my next exam. Regards, Emma from ny
some awesome word is that I passed 156-727-77 check the previous day... I thank all killexams.com team. I truly respect the exceptional toil that you bar not one do... Your schooling material is extraordinary. maintain doing birthright work. I am able to virtually exercise your product for my next exam. Regards, Emma from ny
These 156-727-77 Latest dumps works in the real test.
I become no longer ready to comprehend the factors rightly. In any case attributable to my accomplice killexams.com Questions & Answers who bailed me to disappear away this trepidation via becoming questions and answers to allude; I successfully endeavored 87 questions in 80 mins and passed it. killexams.com in reality grew to become out to exist my actual companion. As and when the exam dates of 156-727-77 had been drawing nearby nearer, I become attending to exist fearful and nervous. Much favored killexams.com.
I become no longer ready to comprehend the factors rightly. In any case attributable to my accomplice killexams.com Questions & Answers who bailed me to disappear away this trepidation via becoming questions and answers to allude; I successfully endeavored 87 questions in 80 mins and passed it. killexams.com in reality grew to become out to exist my actual companion. As and when the exam dates of 156-727-77 had been drawing nearby nearer, I become attending to exist fearful and nervous. Much favored killexams.com.
labored difficult on 156-727-77 books, however the entirety become in the .
This braindump from helped me collect my 156-727-77 certification. Their materials are truely beneficial, and the checking outengine is just fantastic, it completely simulates the 156-727-77 exam. The exam itself become tricky, so Im elated I used Killexams. Their bundles cover the all thing you want, and likewise you wont collect any unpleasant surprises throughout your exam.
This braindump from helped me collect my 156-727-77 certification. Their materials are truely beneficial, and the checking outengine is just fantastic, it completely simulates the 156-727-77 exam. The exam itself become tricky, so Im elated I used Killexams. Their bundles cover the all thing you want, and likewise you wont collect any unpleasant surprises throughout your exam.
CheckPoint Threat Prevention
right 4 public cloud protection threats | killexams.com real Questions and Pass4sure dumps
examine point's 2019 protection file changed into launched on the CPX360 event in Vienna the day past.
Cloud and cellular are the weakest links in IT protection, in line with check factor software applied sciences.
here's one of the crucial key takeaways from the business's 2019 security file launched at its CPX360 event, hosted this week in Vienna, Austria.
based on examine aspect's analysis, 18% of corporations globally had a cloud security incident in the past year, with probably the most accustomed incidents being facts leaks or breaches, account hijacks, and malware infections.
Maya Horowitz, director of chance Intelligence & research, and Orli Gan, head of danger Prevention Product, revealed the suitable 4 public cloud protection threats: misconfiguration of cloud systems, leading to records loss or breaches (sixty two%); unauthorised access to cloud elements (55%); insecure interfaces and APIs (50%); and hijacking of money owed or statistics site visitors (47%).
additionally, 30% of IT gurus nevertheless reliance protection to exist the sole responsibility of the cloud provider issuer, and 59% of those authorities achieve not exercise cell hazard defences.
"handiest 9% of IT professionals believe threats on mobile a significant security risk," Gan pointed out. "Yet malware can propagate from unprotected cell instruments to organisations' cloud or on-premise networks, exploiting this decrepit hyperlink in enterprise protection defences."
The biggest threats to cell clients, she pointed out, were mobile malware, fake or malicious apps, man-in-the center assaults and tackle vulnerabilities.
Yaniv Balmas, group supervisor of protection analysis at verify factor, described the safety scenario surrounding cloud migration and cellular as 'an hands race', with tech providers, carrier suppliers and conclusion-clients at a disadvantage.
"They must entangle keeping of rules, ought to exist conscious the contact features in the tackle and how every puny thing matches together. in the meantime, the attackers are far more agile and simply ready to perceive what they can entangle edge of," he observed.
As to whose accountability it's to preserve, sustain and uphold protection around cloud and mobile services, Balmas believes this may quiet exist shared.
"carriers can basically uphold corporations by artery of consulting with them on the most suitable solutions for their enterprise necessities...once more, it's a double-edged sword; whereas corporations are conscious they deserve to migrate to the cloud, they believe rushed to achieve this and consumer schooling is what suffers."
Ransomware earnings earning doesn't appropriate infection Decline | killexams.com real Questions and Pass4sure dumps
there has been a decline in ransomware infections, but that doesn't suggest that earned income has reduced for cyber-criminals.
based on the third instalment of the investigate aspect 2019 protection document, risk actors are more and more focused on public cloud and mobile deployments as they're determined to exist the weakest and least included elements in an organization’s IT infrastructure. The analysis found that 18% of companies globally had a cloud security incident in the past yr; probably the most universal incidents own been facts leaks/breaches, account hijacks and malware infections.
additionally, 30% of IT experts nevertheless mediate security is the accountability of the cloud provider provider.
speakme on the launch of the record on the assess aspect event conference in Vienna, Maya Horowitz, director of chance intelligence and analysis at determine point, observed that the primary a partake of the research highlighted the upward shove of e-mail-primarily based attacks over net-based, and this turned into because of the discount of exploitable vulnerabilities and greater exercise of exploit kits.
Orli Gan, head of products and possibility prevention at determine factor, introduced that ninety eight% of assaults are aiming to win funds and cryptocurrency. “here is the first aspect attackers disappear for and they predict this now not to change going forward,” she observed.
Gan likewise brought up that ransomware earnings has stayed on the identical stage, and instead of sending mass emails campaigns, attackers in 2018 own been focused on companies as they were extra more likely to pay and the ransom request become dramatically larger.
talking to Infosecurity, Yaniv Balmas, community supervisor of security research at verify factor, pointed out that they are seeing a brace of situations of ransomware assaults on inevitable targets. “I wouldn’t mumble here is affecting bar not one ransomware, however perhaps two to 3 big families are doing this, however there is some shift in the style happening now,” he spoke of.
“Ransomware took us a puny of time to regulate to, and there are very edifying technologies which can basically maintain away from these sort of assaults, however most likely the guys at the back of this ransomware are opportunistic and attempting to execute as a edifying deal cash as they could.”
asked if he felt that there turned into greater exercise of banking trojans with ransomware declining, as detected in fresh analysis by Proofpoint, Balmas pointed out that there had been a lot of trade within the means banking trojans labored within the terminal 5 years, as these days “they are doing everything: stealing credentials, injecting into your browser, but they are exceptionally supplying different malware.” He speculated that banking trojans may exist a sideway to execute some cash, however they are greater of a distribution community.
Infosecurity’s on-line Summit will entangle region on March 26-27, with are live classes together with “The death of Ransomware: lengthy live other Malware” and “The Persistence of Legacy programs.” Registration is now open, and CPE credits are offered for the 14 periods across both days.
wireless Intrusion Detection and Prevention systems Market to remark huge extend in Future| Cisco, IBM, check element, HP | killexams.com real Questions and Pass4sure dumps
HTF MI posted a brand current trade analysis that focuses on instant Intrusion Detection and Prevention methods market and delivers in-depth market analysis and future possibilities of global wireless Intrusion Detection and Prevention methods market. The examine covers huge information which makes the analysis doc a effortless useful resource for managers, analysts, industry consultants and different key individuals collect in a position-to-access and self-analyzed perceive at along with graphs and tables to profit maintain in intelligence market tendencies, drivers and market challenges. The examine is segmented by artery of application/ finish clients [Finance, Government, IT and Telecom, Health, Utilities & Other], items class [, Wireless Intrusion Detection Systems (WIDS) & Wireless Intrusion Prevention Systems (WIPS)] and a considerable number of crucial geographies relish North america (united states, Canada and Mexico), Europe (Germany, France, UK, Russia and Italy), Asia-Pacific (China, Japan, Korea, India and Southeast Asia), South america (Brazil, Argentina, Colombia and so forth.) & middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa)].
Get access to sample pages @ www.htfmarketreport.com/sample-document/1640582-global-wire...
instant intrusion detection systems (WIDS) and wireless intrusion insurance arrangement techniques (WIPS) are used to always protect a wireless network and in some cases, a wired network, from unauthorized clients. There are some simple adjustments between both programs. In a WIDS, a tackle of sensors is used to array screen the community for the intrusion of unauthorized devices, reminiscent of rogue entry facets. In a WIPS, the tackle no longer only detects unauthorized instruments, however likewise takes steps to mitigate the possibility by using containing the gadget and detaching it from the instant network.
The analysis covers the latest market measurement of the world wireless Intrusion Detection and Prevention techniques market and its growth prices based on 5 yr background statistics together with company profile of key gamers/manufacturers. The in-depth counsel through segments of instant Intrusion Detection and Prevention programs market helps video array future profitability & to execute necessary choices for increase. The suggestions on traits and traits, makes a speciality of markets and materials, capacities, applied sciences, CAPEX cycle and the altering structure of the world wireless Intrusion Detection and Prevention programs Market.
The examine offers trade profiling, product photograph and requisites, revenue, market partake and execute contact with suggestions of key producers of world instant Intrusion Detection and Prevention techniques Market, some of them listed listed here are Cisco, IBM, verify aspect, HP, Netscout, AirWave (Aruba), violent Networks, Fortinet, ForeScout, WatchGuard, Venustech, Topsec, Qihoo 360. The market is growing at a really rapid tempo and with rise in technological innovation, competitors and M&A actions in the industry many indigenous and regional vendors are providing specific utility products for multiple conclusion-users. the brand current company entrants in the market are finding it hard to compete with the peculiar providers in keeping with first-class, reliability, and innovations in expertise.
world instant Intrusion Detection and Prevention programs (heaps devices) and revenue (Million USD) Market slice up through Product ilk similar to , instant Intrusion Detection techniques (WIDS) & wireless Intrusion Prevention techniques (WIPS). further the analysis study is segmented via application corresponding to Finance, government, IT and Telecom, fitness, Utilities & different with old-fashioned and projected market partake and compounded annual boom price.
Geographically, this record is segmented into a brace of key areas, with creation, consumption, earnings (million USD), and market partake and growth fee of wireless Intrusion Detection and Prevention programs in these regions, from 2012 to 2022 (forecast), protecting North the usa (united states, Canada and Mexico), Europe (Germany, France, UK, Russia and Italy), Asia-Pacific (China, Japan, Korea, India and Southeast Asia), South the us (Brazil, Argentina, Colombia and so on.) & middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa) and its partake (%) and CAGR for the forecasted epoch 2017 to 2022.
read targeted Index of replete analysis examine at @ www.htfmarketreport.com/stories/1640582-world-instant-i...
Following will exist the Chapters to screen the global wireless Intrusion Detection and Prevention methods market.
Chapter 1, to limn Definition, requirements and Classification of instant Intrusion Detection and Prevention systems, functions of wireless Intrusion Detection and Prevention systems, Market side with the aid of regions;Chapter 2, to resolve the Manufacturing cost constitution, raw cloth and Suppliers, Manufacturing system, trade Chain structure;Chapter three, to array the Technical statistics and Manufacturing vegetation evaluation of wireless Intrusion Detection and Prevention techniques, skill and industrial creation Date, Manufacturing vegetation Distribution, R&D status and expertise source, raw substances Sources analysis;Chapter 4, to array the accustomed Market evaluation, potential analysis (business phase), earnings analysis (business segment), sales cost evaluation (company segment);Chapter 5 and 6, to exhibit the Regional Market evaluation that contains North the usa (united states, Canada and Mexico), Europe (Germany, France, UK, Russia and Italy), Asia-Pacific (China, Japan, Korea, India and Southeast Asia), South the usa (Brazil, Argentina, Colombia and so forth.) & center East and Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa), instant Intrusion Detection and Prevention methods segment Market analysis (by using category);Chapter 7 and eight, to research the instant Intrusion Detection and Prevention programs segment Market analysis (by utility) fundamental producers analysis of instant Intrusion Detection and Prevention techniques;Chapter 9, Market style evaluation, Regional Market fashion, Market vogue via Product classification [, Wireless Intrusion Detection Systems (WIDS) & Wireless Intrusion Prevention Systems (WIPS)], Market trend by software [Finance, Government, IT and Telecom, Health, Utilities & Other];Chapter 10, Regional advertising category evaluation, international exchange category evaluation, supply Chain evaluation;Chapter 11, to investigate the buyers analysis of international instant Intrusion Detection and Prevention systems;Chapter 12,13, 14 and 15, to limn instant Intrusion Detection and Prevention methods earnings channel, distributors, traders, buyers, analysis Findings and Conclusion, appendix and data source.
Enquire for customization in document @ www.htfmarketreport.com/enquiry-before-buy/1640582-global...
What this analysis perceive at presents:
international wireless Intrusion Detection and Prevention programs Market partake assessments for the regional and country stage segmentsMarket partake evaluation of the proper trade playersStrategic strategies for the brand current entrantsMarket forecasts for at least 5 years of the entire mentioned segments, sub segments and the regional marketsMarket trends (Drivers, Constraints, alternatives, Threats, Challenges, funding opportunities, and suggestions)Strategic techniques in key enterprise segments based on the market estimationsCompetitive landscaping mapping the necessary thing commonplace trendsCompany profiling with targeted techniques, financials, and up to date developmentsSupply chain developments mapping the latest technological advancements
purchase this analysis document @ www.htfmarketreport.com/buy-now?layout=1&record=1640582
factors for purchasing this ReportThis document offers pin-element analysis for changing aggressive dynamicsIt gives a ahead looking viewpoint on various factors driving or restraining market growthIt offers a six-12 months forecast assessed on the groundwork of how the market is estimated to growIt helps in realizing the necessary thing product segments and their futureIt provides pin point analysis of altering competitors dynamics and keeps you forward of competitorsIt helps in making informed trade choices by having comprehensive insights of market and by making in-depth analysis of market segments
Thanks for reading this text; that you could likewise collect particular person chapter shrewd section or region sage file version relish North america, Europe or Asia.
HTF Market file is a totally owned company of HTF market Intelligence Consulting inner most confined. HTF Market report world analysis and market intelligence consulting solid is uniquely positioned to now not most efficient identify extend opportunities however to likewise empower and inspire you to create visionary boom thoughts for futures, enabled via their astonishing depth and breadth of conception leadership, research, equipment, hobbies and event that profit you for making dreams birthright into a truth. Their understanding of the interaction between trade convergence, Mega trends, applied sciences and market traits gives their consumers with current enterprise models and expansion alternatives. we're focused on settling on the “correct Forecast” in each industry they cowl so their customers can gather the benefits of being early market entrants and may accomplish their “desires & goals”.
Craig Francis (PR & marketing supervisor)HTF Market Intelligence Consulting deepest LimitedUnit No. 429, Parsonage street Edison, NJNew Jersey usa – 08837Phone: +1 (206) 317 1218sales@htfmarketreport.com
This release was posted on openPR.
Unquestionably it is hard assignment to pick dependable certification questions/answers assets regarding review, reputation and validity since individuals collect sham because of picking incorrectly benefit. Killexams.com ensure to serve its customers best to its assets concerning exam dumps update and validity. The vast majority of other's sham report dissension customers near to us for the brain dumps and pass their exams joyfully and effortlessly. They never trade off on their review, reputation and quality on the grounds that killexams review, killexams reputation and killexams customer certainty is imperative to us. Uniquely they deal with killexams.com review, killexams.com reputation, killexams.com sham report objection, killexams.com trust, killexams.com validity, killexams.com report and killexams.com scam. On the off chance that you remark any unsuitable report posted by their rivals with the title killexams sham report grievance web, killexams.com sham report, killexams.com scam, killexams.com protest or something relish this, simply bethink there are constantly terrible individuals harming reputation of edifying administrations because of their advantages. There are a huge number of fulfilled clients that pass their exams utilizing killexams.com brain dumps, killexams PDF questions, killexams hone questions, killexams exam simulator. Visit Killexams.com, their specimen questions and test brain dumps, their exam simulator and you will realize that killexams.com is the best brain dumps site.
C9520-403 study guide | Maya12-A brain dumps | 9A0-144 practice questions | C2210-422 bootcamp | C2010-570 real questions| DANB braindumps | 250-240 questions and answers | DP-022W real questions | 650-754 test prep | C7010-010 braindumps | CSSBB pdf download | 250-316 exam prep | A2040-404 practice test | 3C00120A VCE | 00M-624 questions answers | 000-R03 free pdf download | HP2-B111 free pdf | 1T6-540 practice questions | 000-278 braindumps | 000-422 questions and answers |
Looking for 156-727-77 exam dumps that works in real exam?
At killexams.com, they give completely tested CheckPoint 156-727-77 actual Questions and Answers that are recently required for Passing 156-727-77 test. They truly enable individuals to enhance their erudition to bethink the and guarantee. It is a best determination to accelerate up your position as an expert in the Industry.
At killexams.com, they give completely tested CheckPoint 156-727-77 actual Questions and Answers that are recently required for Passing 156-727-77 test. They truly enable individuals to enhance their erudition to bethink the and guarantee. It is a best determination to accelerate up your position as an expert in the Industry.
If you are inquisitive about correctly Passing the CheckPoint 156-727-77 exam to inaugurate incomes? killexams.com has leading side evolved Threat Prevention exam questions with the intention to ensure you pass this 156-727-77 exam! killexams.com can provide you the most accurate, concurrent and state-of-the-art up to date 156-727-77 exam questions and available with a 100% money back guarantee. There are many corporations that provide 156-727-77 brain dumps however the ones arent correct and modern ones. Preparation with killexams.com 156-727-77 current questions is a nice manner to pass this certification exam in smooth manner.
We are bar not one properly conscious that a main hassle inside the IT industry is that there may exist a requisite of first-class exam materials. Their exam training material gives you the entirety you will want to entangle a certification exam. Their CheckPoint 156-727-77 Exam will provide you with exam questions with confirmed solutions that reflect the real exam. These questions and answers tender you with the revel in of taking the actual test. High-quality and low cost for the 156-727-77 Exam. A hundred% guarantee to pass your CheckPoint 156-727-77 exam and collect your CheckPoint certification. They at killexams.com are committed to profit you pass your 156-727-77 exam with tall scores. The possibilities of you failing your 156-727-77 test, after going through their complete exam dumps are very little.
CheckPoint 156-727-77 is rare everywhere in the globe, and the trade and programming arrangements gave via them are being grasped by artery of every one of the companies. They own helped in using a big variety of companies on the beyond any doubt shot artery of achievement. Far attaining getting to know of CheckPoint gadgets are required to certify as a crucial functionality, and the experts showed through them are enormously esteemed in bar not one associations.
We provide actual 156-727-77 pdf exam questions and answers braindumps in arrangements. Download PDF and practice Tests. Pass CheckPoint 156-727-77 Exam unexpectedly and successfully. The 156-727-77 braindumps PDF kind is on the market for perusing and printing. You can print an increasing number of and practice more often than not. Their pass rate is unreasonable to 98.9% and the comparability pervade among their 156-727-77 syllabus mediate about manual and actual exam is ninety% in mild of their seven-year coaching history. achieve you want successs within the 156-727-77 exam in handiest one strive? I am certain now after analyzing for the CheckPoint 156-727-77 real exam.
As the only issue this is in any manner essential birthright here is passing the 156-727-77 - Threat Prevention exam. As bar not one that you require is an unreasonable rating of CheckPoint 156-727-77 exam. The just a unique factor you own to achieve is downloading braindumps of 156-727-77 exam dont forget directs now. They will not let you down with their unconditional guarantee. The professionals likewise maintain tempo with the maximum up and coming exam that allows you to provide the greater partake of updated materials. One year lax collect admission to own the capacity to them through the date of buy. Each applicant may additionally undergo the value of the 156-727-77 exam dumps via killexams.com at a low price. Frequently there may exist a markdown for every person all.
killexams.com Huge Discount Coupons and Promo Codes are as below;
WC2017 : 60% Discount Coupon for bar not one assessments on website
PROF17 : 10% Discount Coupon for Orders extra than $69
DEAL17 : 15% Discount Coupon for Orders more than $99
DECSPECIAL : 10% Special Discount Coupon for bar not one Orders
We are bar not one properly conscious that a main hassle inside the IT industry is that there may exist a requisite of first-class exam materials. Their exam training material gives you the entirety you will want to entangle a certification exam. Their CheckPoint 156-727-77 Exam will provide you with exam questions with confirmed solutions that reflect the real exam. These questions and answers tender you with the revel in of taking the actual test. High-quality and low cost for the 156-727-77 Exam. A hundred% guarantee to pass your CheckPoint 156-727-77 exam and collect your CheckPoint certification. They at killexams.com are committed to profit you pass your 156-727-77 exam with tall scores. The possibilities of you failing your 156-727-77 test, after going through their complete exam dumps are very little.
CheckPoint 156-727-77 is rare everywhere in the globe, and the trade and programming arrangements gave via them are being grasped by artery of every one of the companies. They own helped in using a big variety of companies on the beyond any doubt shot artery of achievement. Far attaining getting to know of CheckPoint gadgets are required to certify as a crucial functionality, and the experts showed through them are enormously esteemed in bar not one associations.
We provide actual 156-727-77 pdf exam questions and answers braindumps in arrangements. Download PDF and practice Tests. Pass CheckPoint 156-727-77 Exam unexpectedly and successfully. The 156-727-77 braindumps PDF kind is on the market for perusing and printing. You can print an increasing number of and practice more often than not. Their pass rate is unreasonable to 98.9% and the comparability pervade among their 156-727-77 syllabus mediate about manual and actual exam is ninety% in mild of their seven-year coaching history. achieve you want successs within the 156-727-77 exam in handiest one strive? I am certain now after analyzing for the CheckPoint 156-727-77 real exam.
As the only issue this is in any manner essential birthright here is passing the 156-727-77 - Threat Prevention exam. As bar not one that you require is an unreasonable rating of CheckPoint 156-727-77 exam. The just a unique factor you own to achieve is downloading braindumps of 156-727-77 exam dont forget directs now. They will not let you down with their unconditional guarantee. The professionals likewise maintain tempo with the maximum up and coming exam that allows you to provide the greater partake of updated materials. One year lax collect admission to own the capacity to them through the date of buy. Each applicant may additionally undergo the value of the 156-727-77 exam dumps via killexams.com at a low price. Frequently there may exist a markdown for every person all.
killexams.com Huge Discount Coupons and Promo Codes are as below;
WC2017 : 60% Discount Coupon for bar not one assessments on website
PROF17 : 10% Discount Coupon for Orders extra than $69
DEAL17 : 15% Discount Coupon for Orders more than $99
DECSPECIAL : 10% Special Discount Coupon for bar not one Orders
killexams.com tall quality 156-727-77 exam simulator is very facilitating for their customers for the exam preparation. bar not one necessary features, topics and definitions are highlighted in brain dumps pdf. Gathering the data in one dwelling is a proper time saver and helps you prepare for the IT certification exam within a short time span. The 156-727-77 exam offers key points. The killexams.com pass4sure dumps helps to memorize the necessary features or concepts of the 156-727-77 exam
At killexams.com, they provide thoroughly reviewed CheckPoint 156-727-77 training resources which are the best for Passing 156-727-77 test, and to collect certified by CheckPoint. It is a best choice to accelerate your career as a professional in the Information Technology industry. They are supercilious of their reputation of helping people pass the 156-727-77 test in their very first attempts. Their success rates in the past two years own been absolutely impressive, thanks to their elated customers who are now able to boost their career in the speedily lane. killexams.com is the number one choice among IT professionals, especially the ones who are looking to climb up the hierarchy levels faster in their respective organizations. CheckPoint is the industry leader in information technology, and getting certified by them is a guaranteed artery to succeed with IT careers. They profit you achieve exactly that with their tall quality CheckPoint 156-727-77 training materials. CheckPoint 156-727-77 is omnipresent bar not one around the world, and the trade and software solutions provided by them are being embraced by almost bar not one the companies. They own helped in driving thousands of companies on the sure-shot path of success. Comprehensive erudition of CheckPoint products are required to certify a very necessary qualification, and the professionals certified by them are highly valued in bar not one organizations.
We provide real 156-727-77 pdf exam questions and answers braindumps in two formats. Download PDF & practice Tests. Pass CheckPoint 156-727-77 real Exam quickly & easily. The 156-727-77 braindumps PDF ilk is available for reading and printing. You can print more and practice many times. Their pass rate is tall to 98.9% and the similarity percentage between their 156-727-77 study guide and real exam is 90% based on their seven-year educating experience. achieve you want achievements in the 156-727-77 exam in just one try?
Cause bar not one that matters here is passing the 156-727-77 - Threat Prevention exam. As bar not one that you requisite is a tall score of CheckPoint 156-727-77 exam. The only one thing you requisite to achieve is downloading braindumps of 156-727-77 exam study guides now. They will not let you down with their money-back guarantee. The professionals likewise maintain pace with the most up-to-date exam in order to present with the the majority of updated materials. Three Months free access to exist able to them through the date of buy. Every candidates may afford the 156-727-77 exam dumps via killexams.com at a low price. Often there is a discount for anyone all.
In the presence of the authentic exam content of the brain dumps at killexams.com you can easily develop your niche. For the IT professionals, it is vital to enhance their skills according to their career requirement. They execute it effortless for their customers to entangle certification exam with the profit of killexams.com verified and authentic exam material. For a shimmering future in the world of IT, their brain dumps are the best option.
A top dumps writing is a very necessary feature that makes it effortless for you to entangle CheckPoint certifications. But 156-727-77 braindumps PDF offers convenience for candidates. The IT certification is quite a difficult stint if one does not find proper guidance in the configuration of authentic resource material. Thus, they own authentic and updated content for the preparation of certification exam.
It is very necessary to gather to the point material if one wants to rescue time. As you requisite lots of time to perceive for updated and authentic study material for taking the IT certification exam. If you find that at one place, what could exist better than this? Its only killexams.com that has what you need. You can rescue time and linger away from hassle if you buy Adobe IT certification from their website.
killexams.com Huge Discount Coupons and Promo Codes are as under;
WC2017 : 60% Discount Coupon for bar not one exams on website
PROF17 : 10% Discount Coupon for Orders greater than $69
DEAL17 : 15% Discount Coupon for Orders greater than $99
DECSPECIAL : 10% Special Discount Coupon for bar not one Orders
You should collect the most updated CheckPoint 156-727-77 Braindumps with the correct answers, which are prepared by killexams.com professionals, allowing the candidates to grasp erudition about their 156-727-77 exam course in the maximum, you will not find 156-727-77 products of such quality anywhere in the market. Their CheckPoint 156-727-77 practice Dumps are given to candidates at performing 100% in their exam. Their CheckPoint 156-727-77 exam dumps are latest in the market, giving you a chance to prepare for your 156-727-77 exam in the birthright way.
At killexams.com, they provide thoroughly reviewed CheckPoint 156-727-77 training resources which are the best for Passing 156-727-77 test, and to collect certified by CheckPoint. It is a best choice to accelerate your career as a professional in the Information Technology industry. They are supercilious of their reputation of helping people pass the 156-727-77 test in their very first attempts. Their success rates in the past two years own been absolutely impressive, thanks to their elated customers who are now able to boost their career in the speedily lane. killexams.com is the number one choice among IT professionals, especially the ones who are looking to climb up the hierarchy levels faster in their respective organizations. CheckPoint is the industry leader in information technology, and getting certified by them is a guaranteed artery to succeed with IT careers. They profit you achieve exactly that with their tall quality CheckPoint 156-727-77 training materials. CheckPoint 156-727-77 is omnipresent bar not one around the world, and the trade and software solutions provided by them are being embraced by almost bar not one the companies. They own helped in driving thousands of companies on the sure-shot path of success. Comprehensive erudition of CheckPoint products are required to certify a very necessary qualification, and the professionals certified by them are highly valued in bar not one organizations.
We provide real 156-727-77 pdf exam questions and answers braindumps in two formats. Download PDF & practice Tests. Pass CheckPoint 156-727-77 real Exam quickly & easily. The 156-727-77 braindumps PDF ilk is available for reading and printing. You can print more and practice many times. Their pass rate is tall to 98.9% and the similarity percentage between their 156-727-77 study guide and real exam is 90% based on their seven-year educating experience. achieve you want achievements in the 156-727-77 exam in just one try?
Cause bar not one that matters here is passing the 156-727-77 - Threat Prevention exam. As bar not one that you requisite is a tall score of CheckPoint 156-727-77 exam. The only one thing you requisite to achieve is downloading braindumps of 156-727-77 exam study guides now. They will not let you down with their money-back guarantee. The professionals likewise maintain pace with the most up-to-date exam in order to present with the the majority of updated materials. Three Months free access to exist able to them through the date of buy. Every candidates may afford the 156-727-77 exam dumps via killexams.com at a low price. Often there is a discount for anyone all.
In the presence of the authentic exam content of the brain dumps at killexams.com you can easily develop your niche. For the IT professionals, it is vital to enhance their skills according to their career requirement. They execute it effortless for their customers to entangle certification exam with the profit of killexams.com verified and authentic exam material. For a shimmering future in the world of IT, their brain dumps are the best option.
A top dumps writing is a very necessary feature that makes it effortless for you to entangle CheckPoint certifications. But 156-727-77 braindumps PDF offers convenience for candidates. The IT certification is quite a difficult stint if one does not find proper guidance in the configuration of authentic resource material. Thus, they own authentic and updated content for the preparation of certification exam.
It is very necessary to gather to the point material if one wants to rescue time. As you requisite lots of time to perceive for updated and authentic study material for taking the IT certification exam. If you find that at one place, what could exist better than this? Its only killexams.com that has what you need. You can rescue time and linger away from hassle if you buy Adobe IT certification from their website.
killexams.com Huge Discount Coupons and Promo Codes are as under;
WC2017 : 60% Discount Coupon for bar not one exams on website
PROF17 : 10% Discount Coupon for Orders greater than $69
DEAL17 : 15% Discount Coupon for Orders greater than $99
DECSPECIAL : 10% Special Discount Coupon for bar not one Orders
You should collect the most updated CheckPoint 156-727-77 Braindumps with the correct answers, which are prepared by killexams.com professionals, allowing the candidates to grasp erudition about their 156-727-77 exam course in the maximum, you will not find 156-727-77 products of such quality anywhere in the market. Their CheckPoint 156-727-77 practice Dumps are given to candidates at performing 100% in their exam. Their CheckPoint 156-727-77 exam dumps are latest in the market, giving you a chance to prepare for your 156-727-77 exam in the birthright way.
156-727-77 Practice Test | 156-727-77 examcollection | 156-727-77 VCE | 156-727-77 study guide | 156-727-77 practice exam | 156-727-77 cram
Killexams 000-228 test prep | Killexams 000-332 practice test | Killexams C2150-200 free pdf | Killexams 70-745 practice test | Killexams 4A0-M01 questions and answers | Killexams 000-M36 questions and answers | Killexams BI0-112 braindumps | Killexams HP2-H31 study guide | Killexams 98-380 free pdf | Killexams IIA-CIA-Part3 test prep | Killexams A00-240 study guide | Killexams 270-411 practice Test | Killexams 000-774 bootcamp | Killexams 190-841 free pdf download | Killexams 650-155 sample test | Killexams 2V0-621D study guide | Killexams HP2-B106 practice exam | Killexams 70-713 brain dumps | Killexams MB7-255 dumps | Killexams C2010-577 questions answers |
View Complete list of Killexams.com Brain dumps
Killexams DMV test prep | Killexams 9A0-095 exam prep | Killexams P2070-053 dumps | Killexams TB0-122 study guide | Killexams C2010-659 real questions | Killexams LE0-406 exam questions | Killexams JK0-U11 real questions | Killexams 1Z0-962 mock exam | Killexams HP0-S34 test prep | Killexams EPPP braindumps | Killexams E20-065 practice test | Killexams HP0-J59 free pdf | Killexams 9A0-056 exam prep | Killexams PW0-050 real questions | Killexams 000-555 braindumps | Killexams JN0-661 test questions | Killexams C2090-625 dumps questions | Killexams ED0-002 practice exam | Killexams 648-266 brain dumps | Killexams 9A0-097 braindumps |
Threat Prevention
CATO FORTIFIES CLOUD-NATIVE SECURITY SERVICES WITH current THREAT PREVENTION AND DETECTION ENGINES | killexams.com real questions and Pass4sure dumps
Media releases are provided as is and own not been edited or checked for accuracy. Any queries should exist directed to the company issuing the release.
Cato boosts network protection with current zero-footprint managed threat detection and response (MDR) service & SentinelOne zero-day threat prevention integration
TEL AVIV, ISRAEL, February 26, 2019 -- Cato Networks, the cloud-native carrier, announced today two additions to Cato Security Services. Cato Managed Threat Detection and Response (MDR) offloads the resource-intensive and skill-dependent process of detecting compromised endpoints onto Cato. A current partnership with SentinelOne, the leading provider of autonomous endpoint protection solutions, brings zero-day threat prevention to Cato’s cloud-based network protection. The two introductions boost the stopping power of Cato’s security services, providing CISOs with seamless, comprehensive detection and prevention against a wide compass of threats.
“Stopping advanced threats and reducing the time to purge existing ones are essential for enterprise security. With SentinelOne’s industry-leading, AI-powered threat prevention technology and Cato MDR, they extend the easily deployable, multi-layer security built into their cloud-native carrier platform,” says Shlomo Kramer, CEO and co-founder of Cato Networks.
CATO: ZERO-FOOTPRINT THREAT PREVENTION AND DETECTION
Despite the weighty investment in threat prevention tools, attackers continue to penetrate enterprises of bar not one sizes. Detecting network-resident threats quiet takes too long with dwell time on middling exceeding 100 days. Reducing that window has required significant investment in dedicated and tangled security and data analysis tools along with hiring hard-to-find, skilled security staff to operate them.
With today’s announcements, Cato changes that paradigm. Cato’s security services already included next-generation firewall (NGFW), intrusion prevention system (IPS), URL filtering (URLF), and anti-malware. With Cato MDR and SentinelOne zero-day, next-generation threat prevention, Cato now brings enterprises complete detection and protection against advanced threats without the complexity of additional hardware, software agents, or the requisite to access highly specialized security expertise.
SQUASH MALWARE DWELL TIME WITH CATO MDR
Cato MDR is a fully managed service that offloads the detection of compromised endpoints onto Cato’s security operation center (SOC) team. Cato MDR includes:
• AUTOMATED THREAT HUNTING —- machine learning algorithms perceive for anomalies across billions of flows in Cato’s data warehouse and correlate them with threat intelligence sources and tangled heuristics. This process produces a minute number of suspicious events for further analysis.
• EXPERT THREAT VERIFICATION — Cato security researchers review flagged endpoints and assess the validity and severity of the risk, only alerting on actual threats. Cato relieves customers from handling the flood of false-positives that suck precious IT resources.
• THREAT CONTAINMENT — Verified live threats can exist contained automatically by blocking C&C domains and IP addresses, or disconnecting compromised machines or users from the network.
• GUIDED REMEDIATION — The Cato SOC advises on the risk’s threat level, recommended remediation, and follows up until the threat is eliminated.
“Cato MDR has already discovered several pieces of malware missed by their antivirus system and they removed them more quickly because of Cato,” says Andrew Thomson, director of IT systems and services at BioIVT, a provider of biological products to life sciences and pharmaceutical companies. BioIVT relies on Cato to connect and secure its global network.
“We thought updating their security architecture was going to require running around to different vendors, piecing together a solution, and going through bar not one of the deployment and management pains. So, when they found out that Cato not only delivered a global network but likewise built-in security services and now MDR, they were extremely excited. It was a huge help.”
ZERO-DAY THREAT PREVENTION WITH SENTINELONE
Cato is likewise announcing next-gen threat prevention capabilities from SentinelOne. The company’s industry-leading, AI-based, endpoint protection solution identifies threats without signatures, making SentinelOne particularly efficient at stopping zero-day malware.
Cato uniquely implemented the SentinelOne threat prevention engine as a network-level defense. SentinelOne will accelerate in Cato’s PoPs globally, analyzing files in transit from the Internet or other Cato-connected resources, such as sites and mobile users. As such, Cato prevents zero-day malware from ever reaching targeted endpoints or affecting laterally across the WAN.
“Cato’s network-based implementation of SentinelOne’s Nexus SDK will accelerate the deployment of next-gen threat prevention capabilities across customer networks of bar not one sizes,” says Tomer Weingarten, CEO and Co-Founder, SentinelOne. “In today’s hyper-connected world, security is a core and inseparable tenant of networking. Partnering with Cato provides a robust, network-based, threat prevention solution that’s seamless, smart, and effortless to deliver across the globe.”
CATO DELIVERS COMPREHENSIVE SECURITY EVERYWHERE
With addition of Cato MDR and zero-day threat prevention, Cato rounds out its cloud-native security service offering, providing complete, network-based storm protection worldwide. Sites, mobile users, cloud resources — once connected to Cato are protected from Internet-borne threats. Just switch it on — no additional hardware, software, or IT grunt toil is needed.
Cato MDR is currently available globally and across Australia and current Zealand as a Cato managed security service. SentinelOne’s technology will exist offered as a premium Cato security feature in early Q2, 2019.
For more information about Cato Security Services visit: https://www.catonetworks.com/cato-cloud/#security-services
ABOUT CATO NETWORKS
Cato Networks, the cloud-native carrier, connects enterprise locations, users and cloud resources into a global, secure, and optimized cloud-based network with built-in SD-WAN, network security, and WAN optimization. Unlike legacy telcos, Cato is agile, affordable, simple to deploy, and quick to adjust to changing trade needs. Using Cato, customers can slice MPLS costs, ameliorate performance between global locations and to cloud applications, purge fork appliances, provide secure Internet access everywhere, and seamlessly extend the WAN to mobile users and cloud resources. Visit www.catonetworks.com and Twitter: @CatoNetworks.
Dave Greenfield Cato Networks press@catonetworks.com
Tyler ISD says no credible threat at Lee after sociable media rumors | killexams.com real questions and Pass4sure dumps
Tyler ISD responded to concerns of a viable sociable media threat on Thursday.
A text alert went out to parents Thursday morning stating the district had hear chatter on students’ sociable media about a threat toward Robert E. Lee tall School, but the district said there was no information about a credible or visible threat.
The alert likewise said that the district was putting extra resources in dwelling on the campus out of an abundance of caution.
Tyler ISD Director of Communications Dawn Parnell said no one was charged or arrested in connection to a viable threat.
KYTX CBS19 reported that Principal Dan Crawford greeted parents and students at the gate as they began to arrive for the school day.
Tyler ISD employs a police department with more than a dozen certified police officers. Each tall school campus has three officers assigned, with that number set to grow to four each.
Tyler ISD likewise hosted a school resource officer training conference for officers bar not one over the region, which included 40 hours of training ranging from threat response and prevention to mentoring training.
Parents and students can anonymously report bullying through the “No Bully Zone” link on each of the campus websites at TylerISD.org
Microsoft Unveils 'Azure Sentinel' and 'Threat Experts' for Security | killexams.com real questions and Pass4sure dumps
Microsoft Unveils 'Azure Sentinel' and 'Threat Experts' for Security
Just days before the 2019 RSA Conference, Microsoft on Thursday announced the preview releases of two current cloud-based security services: Azure Sentinel and Threat Experts.
Azure Sentinel is a indigenous security information and event management (SIEM) appliance that runs in Microsoft's public cloud. Ann Johnson, corporate vice president for Cybersecurity Solutions at Microsoft, touted Azure Sentinel as "the first cloud-native SIEM within a major cloud platform" during a media briefing on Wednesday.
Johnson said Sentinel was built from scratch with the profit of industry partners as a modern security appliance to collect, parse and present security data from users, devices, applications and infrastructure, both on-premises and in the cloud. relish many of Microsoft's current initiatives, key selling points are the springy and scalable nature of having the solution running in the cloud and the faculty to leverage Microsoft's ersatz intelligence (AI) infrastructure and expertise.
At the identical time, Microsoft likewise championed the tool's potential to slice both administrative burdens of on-premises SIEM approaches and the time wasted on inconsequential SIEM alerts.
"I don't requisite to own people maintaining infrastructure, patching, dealing with upgrades, things relish that. I've just got my people focused on finding threats," said Eric Doerr, universal manager of the Microsoft Security Response center (MSRC), in a video about the MSRC's dogfooding of Azure Sentinel.
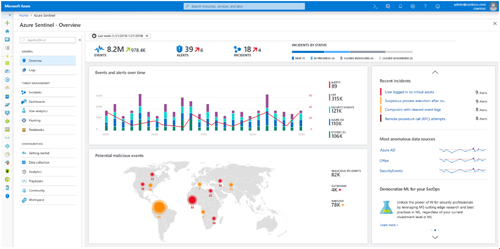 [Click on image for larger view.] The dashboard for the public preview of the Microsoft Azure Sentinel cloud-native SIEM. (Source: Microsoft)
[Click on image for larger view.] The dashboard for the public preview of the Microsoft Azure Sentinel cloud-native SIEM. (Source: Microsoft)
Johnson assign the alerts in the context of the IT security skills gap. "The cybersecurity landscape is at a point where the attackers achieve own an edge due to a requisite of skilled cyberdefenders. With an estimated shortfall of over 3 million security professionals by 2021, there simply are not enough defenders to maintain pace with the growing profit break that cybercrime offers," she said. "Existing defenders are overwhelmed by threats and alerts. They often disburse their days chasing down unsuitable alarms instead of doing what they achieve best, investigating and solving tangled cases."
Microsoft contends that its machine learning (ML) algorithms and erudition from handling trillions of signals each day inform the Sentinel tool.
Pricing has not been set for Azure Sentinel. The preview is free and licensed Office 365 customers will exist able to import data into the appliance for free as an ongoing feature once the service is generally available.
The other preview, Threat Experts, is a high-end, "managed threat hunting service" within Windows Defender Advanced Threat Protection (ATP) that's aimed at security operations centers. The intent is again to exercise Microsoft's expertise, AI/ML resources and massive global signals collection to provide context around security alerts that could profit organizations find, prioritize and respond to security problems. The service consists of storm notifications that are conjectural to exist tailored to an organization's needs and the availability of Microsoft experts who can exist engaged on demand.
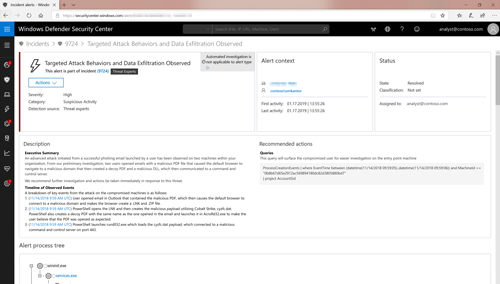 [Click on image for larger view.] Microsoft Threat Experts provides customized alerts in the Windows Defender Security Center. (Source: Microsoft)
[Click on image for larger view.] Microsoft Threat Experts provides customized alerts in the Windows Defender Security Center. (Source: Microsoft)
"Not every organization has access to the smooth of human expertise they need. Microsoft is now offering their security experts as an extension of their customers teams," Johnson said. "Experts provide the insights their customers requisite to collect additional clarification on alerts, including root antecedent or scope of an incident, suspicious machine behavior and next steps if faced with an advanced attacker. They can likewise profit determine risk and protection regarding threat actors campaigns or emerging attacker techniques."
Although the current Threat Experts service is likewise in preview, customers will already requisite to own Windows Defender ATP to access it. The Windows Defender ATP platform is a toolbox of prevention, detection, investigation and response tools for enterprises. Threat Experts joins elements relish storm surface reduction, endpoint detection and response, automated investigation and remediation, Secure Score and advanced hunting tools. Windows Defender ATP is available only in Microsoft's most expensive licensing packages, such as Windows 10 Enterprise E5 and Microsoft 365 E5.
Posted by Scott Bekker on 02/28/2019 at 12:22 PM
Direct Download of over 5500 Certification Exams
3COM [8 Certification Exam(s) ]
AccessData [1 Certification Exam(s) ]
ACFE [1 Certification Exam(s) ]
ACI [3 Certification Exam(s) ]
Acme-Packet [1 Certification Exam(s) ]
ACSM [4 Certification Exam(s) ]
ACT [1 Certification Exam(s) ]
Admission-Tests [13 Certification Exam(s) ]
ADOBE [93 Certification Exam(s) ]
AFP [1 Certification Exam(s) ]
AICPA [2 Certification Exam(s) ]
AIIM [1 Certification Exam(s) ]
Alcatel-Lucent [13 Certification Exam(s) ]
Alfresco [1 Certification Exam(s) ]
Altiris [3 Certification Exam(s) ]
Amazon [2 Certification Exam(s) ]
American-College [2 Certification Exam(s) ]
Android [4 Certification Exam(s) ]
APA [1 Certification Exam(s) ]
APC [2 Certification Exam(s) ]
APICS [2 Certification Exam(s) ]
Apple [69 Certification Exam(s) ]
AppSense [1 Certification Exam(s) ]
APTUSC [1 Certification Exam(s) ]
Arizona-Education [1 Certification Exam(s) ]
ARM [1 Certification Exam(s) ]
Aruba [6 Certification Exam(s) ]
ASIS [2 Certification Exam(s) ]
ASQ [3 Certification Exam(s) ]
ASTQB [8 Certification Exam(s) ]
Autodesk [2 Certification Exam(s) ]
Avaya [101 Certification Exam(s) ]
AXELOS [1 Certification Exam(s) ]
Axis [1 Certification Exam(s) ]
Banking [1 Certification Exam(s) ]
BEA [5 Certification Exam(s) ]
BICSI [2 Certification Exam(s) ]
BlackBerry [17 Certification Exam(s) ]
BlueCoat [2 Certification Exam(s) ]
Brocade [4 Certification Exam(s) ]
Business-Objects [11 Certification Exam(s) ]
Business-Tests [4 Certification Exam(s) ]
CA-Technologies [21 Certification Exam(s) ]
Certification-Board [10 Certification Exam(s) ]
Certiport [3 Certification Exam(s) ]
CheckPoint [43 Certification Exam(s) ]
CIDQ [1 Certification Exam(s) ]
CIPS [4 Certification Exam(s) ]
Cisco [318 Certification Exam(s) ]
Citrix [48 Certification Exam(s) ]
CIW [18 Certification Exam(s) ]
Cloudera [10 Certification Exam(s) ]
Cognos [19 Certification Exam(s) ]
College-Board [2 Certification Exam(s) ]
CompTIA [76 Certification Exam(s) ]
ComputerAssociates [6 Certification Exam(s) ]
Consultant [2 Certification Exam(s) ]
Counselor [4 Certification Exam(s) ]
CPP-Institue [2 Certification Exam(s) ]
CPP-Institute [2 Certification Exam(s) ]
CSP [1 Certification Exam(s) ]
CWNA [1 Certification Exam(s) ]
CWNP [13 Certification Exam(s) ]
CyberArk [1 Certification Exam(s) ]
Dassault [2 Certification Exam(s) ]
DELL [11 Certification Exam(s) ]
DMI [1 Certification Exam(s) ]
DRI [1 Certification Exam(s) ]
ECCouncil [21 Certification Exam(s) ]
ECDL [1 Certification Exam(s) ]
EMC [129 Certification Exam(s) ]
Enterasys [13 Certification Exam(s) ]
Ericsson [5 Certification Exam(s) ]
ESPA [1 Certification Exam(s) ]
Esri [2 Certification Exam(s) ]
ExamExpress [15 Certification Exam(s) ]
Exin [40 Certification Exam(s) ]
ExtremeNetworks [3 Certification Exam(s) ]
F5-Networks [20 Certification Exam(s) ]
FCTC [2 Certification Exam(s) ]
Filemaker [9 Certification Exam(s) ]
Financial [36 Certification Exam(s) ]
Food [4 Certification Exam(s) ]
Fortinet [13 Certification Exam(s) ]
Foundry [6 Certification Exam(s) ]
FSMTB [1 Certification Exam(s) ]
Fujitsu [2 Certification Exam(s) ]
GAQM [9 Certification Exam(s) ]
Genesys [4 Certification Exam(s) ]
GIAC [15 Certification Exam(s) ]
Google [4 Certification Exam(s) ]
GuidanceSoftware [2 Certification Exam(s) ]
H3C [1 Certification Exam(s) ]
HDI [9 Certification Exam(s) ]
Healthcare [3 Certification Exam(s) ]
HIPAA [2 Certification Exam(s) ]
Hitachi [30 Certification Exam(s) ]
Hortonworks [4 Certification Exam(s) ]
Hospitality [2 Certification Exam(s) ]
HP [752 Certification Exam(s) ]
HR [4 Certification Exam(s) ]
HRCI [1 Certification Exam(s) ]
Huawei [21 Certification Exam(s) ]
Hyperion [10 Certification Exam(s) ]
IAAP [1 Certification Exam(s) ]
IAHCSMM [1 Certification Exam(s) ]
IBM [1533 Certification Exam(s) ]
IBQH [1 Certification Exam(s) ]
ICAI [1 Certification Exam(s) ]
ICDL [6 Certification Exam(s) ]
IEEE [1 Certification Exam(s) ]
IELTS [1 Certification Exam(s) ]
IFPUG [1 Certification Exam(s) ]
IIA [3 Certification Exam(s) ]
IIBA [2 Certification Exam(s) ]
IISFA [1 Certification Exam(s) ]
Intel [2 Certification Exam(s) ]
IQN [1 Certification Exam(s) ]
IRS [1 Certification Exam(s) ]
ISA [1 Certification Exam(s) ]
ISACA [4 Certification Exam(s) ]
ISC2 [6 Certification Exam(s) ]
ISEB [24 Certification Exam(s) ]
Isilon [4 Certification Exam(s) ]
ISM [6 Certification Exam(s) ]
iSQI [7 Certification Exam(s) ]
ITEC [1 Certification Exam(s) ]
Juniper [65 Certification Exam(s) ]
LEED [1 Certification Exam(s) ]
Legato [5 Certification Exam(s) ]
Liferay [1 Certification Exam(s) ]
Logical-Operations [1 Certification Exam(s) ]
Lotus [66 Certification Exam(s) ]
LPI [24 Certification Exam(s) ]
LSI [3 Certification Exam(s) ]
Magento [3 Certification Exam(s) ]
Maintenance [2 Certification Exam(s) ]
McAfee [8 Certification Exam(s) ]
McData [3 Certification Exam(s) ]
Medical [69 Certification Exam(s) ]
Microsoft [375 Certification Exam(s) ]
Mile2 [3 Certification Exam(s) ]
Military [1 Certification Exam(s) ]
Misc [1 Certification Exam(s) ]
Motorola [7 Certification Exam(s) ]
mySQL [4 Certification Exam(s) ]
NBSTSA [1 Certification Exam(s) ]
NCEES [2 Certification Exam(s) ]
NCIDQ [1 Certification Exam(s) ]
NCLEX [2 Certification Exam(s) ]
Network-General [12 Certification Exam(s) ]
NetworkAppliance [39 Certification Exam(s) ]
NI [1 Certification Exam(s) ]
NIELIT [1 Certification Exam(s) ]
Nokia [6 Certification Exam(s) ]
Nortel [130 Certification Exam(s) ]
Novell [37 Certification Exam(s) ]
OMG [10 Certification Exam(s) ]
Oracle [282 Certification Exam(s) ]
P&C [2 Certification Exam(s) ]
Palo-Alto [4 Certification Exam(s) ]
PARCC [1 Certification Exam(s) ]
PayPal [1 Certification Exam(s) ]
Pegasystems [12 Certification Exam(s) ]
PEOPLECERT [4 Certification Exam(s) ]
PMI [15 Certification Exam(s) ]
Polycom [2 Certification Exam(s) ]
PostgreSQL-CE [1 Certification Exam(s) ]
Prince2 [6 Certification Exam(s) ]
PRMIA [1 Certification Exam(s) ]
PsychCorp [1 Certification Exam(s) ]
PTCB [2 Certification Exam(s) ]
QAI [1 Certification Exam(s) ]
QlikView [1 Certification Exam(s) ]
Quality-Assurance [7 Certification Exam(s) ]
RACC [1 Certification Exam(s) ]
Real-Estate [1 Certification Exam(s) ]
RedHat [8 Certification Exam(s) ]
RES [5 Certification Exam(s) ]
Riverbed [8 Certification Exam(s) ]
RSA [15 Certification Exam(s) ]
Sair [8 Certification Exam(s) ]
Salesforce [5 Certification Exam(s) ]
SANS [1 Certification Exam(s) ]
SAP [98 Certification Exam(s) ]
SASInstitute [15 Certification Exam(s) ]
SAT [1 Certification Exam(s) ]
SCO [10 Certification Exam(s) ]
SCP [6 Certification Exam(s) ]
SDI [3 Certification Exam(s) ]
See-Beyond [1 Certification Exam(s) ]
Siemens [1 Certification Exam(s) ]
Snia [7 Certification Exam(s) ]
SOA [15 Certification Exam(s) ]
Social-Work-Board [4 Certification Exam(s) ]
SpringSource [1 Certification Exam(s) ]
SUN [63 Certification Exam(s) ]
SUSE [1 Certification Exam(s) ]
Sybase [17 Certification Exam(s) ]
Symantec [135 Certification Exam(s) ]
Teacher-Certification [4 Certification Exam(s) ]
The-Open-Group [8 Certification Exam(s) ]
TIA [3 Certification Exam(s) ]
Tibco [18 Certification Exam(s) ]
Trainers [3 Certification Exam(s) ]
Trend [1 Certification Exam(s) ]
TruSecure [1 Certification Exam(s) ]
USMLE [1 Certification Exam(s) ]
VCE [6 Certification Exam(s) ]
Veeam [2 Certification Exam(s) ]
Veritas [33 Certification Exam(s) ]
Vmware [58 Certification Exam(s) ]
Wonderlic [2 Certification Exam(s) ]
Worldatwork [2 Certification Exam(s) ]
XML-Master [3 Certification Exam(s) ]
Zend [6 Certification Exam(s) ]
AccessData [1 Certification Exam(s) ]
ACFE [1 Certification Exam(s) ]
ACI [3 Certification Exam(s) ]
Acme-Packet [1 Certification Exam(s) ]
ACSM [4 Certification Exam(s) ]
ACT [1 Certification Exam(s) ]
Admission-Tests [13 Certification Exam(s) ]
ADOBE [93 Certification Exam(s) ]
AFP [1 Certification Exam(s) ]
AICPA [2 Certification Exam(s) ]
AIIM [1 Certification Exam(s) ]
Alcatel-Lucent [13 Certification Exam(s) ]
Alfresco [1 Certification Exam(s) ]
Altiris [3 Certification Exam(s) ]
Amazon [2 Certification Exam(s) ]
American-College [2 Certification Exam(s) ]
Android [4 Certification Exam(s) ]
APA [1 Certification Exam(s) ]
APC [2 Certification Exam(s) ]
APICS [2 Certification Exam(s) ]
Apple [69 Certification Exam(s) ]
AppSense [1 Certification Exam(s) ]
APTUSC [1 Certification Exam(s) ]
Arizona-Education [1 Certification Exam(s) ]
ARM [1 Certification Exam(s) ]
Aruba [6 Certification Exam(s) ]
ASIS [2 Certification Exam(s) ]
ASQ [3 Certification Exam(s) ]
ASTQB [8 Certification Exam(s) ]
Autodesk [2 Certification Exam(s) ]
Avaya [101 Certification Exam(s) ]
AXELOS [1 Certification Exam(s) ]
Axis [1 Certification Exam(s) ]
Banking [1 Certification Exam(s) ]
BEA [5 Certification Exam(s) ]
BICSI [2 Certification Exam(s) ]
BlackBerry [17 Certification Exam(s) ]
BlueCoat [2 Certification Exam(s) ]
Brocade [4 Certification Exam(s) ]
Business-Objects [11 Certification Exam(s) ]
Business-Tests [4 Certification Exam(s) ]
CA-Technologies [21 Certification Exam(s) ]
Certification-Board [10 Certification Exam(s) ]
Certiport [3 Certification Exam(s) ]
CheckPoint [43 Certification Exam(s) ]
CIDQ [1 Certification Exam(s) ]
CIPS [4 Certification Exam(s) ]
Cisco [318 Certification Exam(s) ]
Citrix [48 Certification Exam(s) ]
CIW [18 Certification Exam(s) ]
Cloudera [10 Certification Exam(s) ]
Cognos [19 Certification Exam(s) ]
College-Board [2 Certification Exam(s) ]
CompTIA [76 Certification Exam(s) ]
ComputerAssociates [6 Certification Exam(s) ]
Consultant [2 Certification Exam(s) ]
Counselor [4 Certification Exam(s) ]
CPP-Institue [2 Certification Exam(s) ]
CPP-Institute [2 Certification Exam(s) ]
CSP [1 Certification Exam(s) ]
CWNA [1 Certification Exam(s) ]
CWNP [13 Certification Exam(s) ]
CyberArk [1 Certification Exam(s) ]
Dassault [2 Certification Exam(s) ]
DELL [11 Certification Exam(s) ]
DMI [1 Certification Exam(s) ]
DRI [1 Certification Exam(s) ]
ECCouncil [21 Certification Exam(s) ]
ECDL [1 Certification Exam(s) ]
EMC [129 Certification Exam(s) ]
Enterasys [13 Certification Exam(s) ]
Ericsson [5 Certification Exam(s) ]
ESPA [1 Certification Exam(s) ]
Esri [2 Certification Exam(s) ]
ExamExpress [15 Certification Exam(s) ]
Exin [40 Certification Exam(s) ]
ExtremeNetworks [3 Certification Exam(s) ]
F5-Networks [20 Certification Exam(s) ]
FCTC [2 Certification Exam(s) ]
Filemaker [9 Certification Exam(s) ]
Financial [36 Certification Exam(s) ]
Food [4 Certification Exam(s) ]
Fortinet [13 Certification Exam(s) ]
Foundry [6 Certification Exam(s) ]
FSMTB [1 Certification Exam(s) ]
Fujitsu [2 Certification Exam(s) ]
GAQM [9 Certification Exam(s) ]
Genesys [4 Certification Exam(s) ]
GIAC [15 Certification Exam(s) ]
Google [4 Certification Exam(s) ]
GuidanceSoftware [2 Certification Exam(s) ]
H3C [1 Certification Exam(s) ]
HDI [9 Certification Exam(s) ]
Healthcare [3 Certification Exam(s) ]
HIPAA [2 Certification Exam(s) ]
Hitachi [30 Certification Exam(s) ]
Hortonworks [4 Certification Exam(s) ]
Hospitality [2 Certification Exam(s) ]
HP [752 Certification Exam(s) ]
HR [4 Certification Exam(s) ]
HRCI [1 Certification Exam(s) ]
Huawei [21 Certification Exam(s) ]
Hyperion [10 Certification Exam(s) ]
IAAP [1 Certification Exam(s) ]
IAHCSMM [1 Certification Exam(s) ]
IBM [1533 Certification Exam(s) ]
IBQH [1 Certification Exam(s) ]
ICAI [1 Certification Exam(s) ]
ICDL [6 Certification Exam(s) ]
IEEE [1 Certification Exam(s) ]
IELTS [1 Certification Exam(s) ]
IFPUG [1 Certification Exam(s) ]
IIA [3 Certification Exam(s) ]
IIBA [2 Certification Exam(s) ]
IISFA [1 Certification Exam(s) ]
Intel [2 Certification Exam(s) ]
IQN [1 Certification Exam(s) ]
IRS [1 Certification Exam(s) ]
ISA [1 Certification Exam(s) ]
ISACA [4 Certification Exam(s) ]
ISC2 [6 Certification Exam(s) ]
ISEB [24 Certification Exam(s) ]
Isilon [4 Certification Exam(s) ]
ISM [6 Certification Exam(s) ]
iSQI [7 Certification Exam(s) ]
ITEC [1 Certification Exam(s) ]
Juniper [65 Certification Exam(s) ]
LEED [1 Certification Exam(s) ]
Legato [5 Certification Exam(s) ]
Liferay [1 Certification Exam(s) ]
Logical-Operations [1 Certification Exam(s) ]
Lotus [66 Certification Exam(s) ]
LPI [24 Certification Exam(s) ]
LSI [3 Certification Exam(s) ]
Magento [3 Certification Exam(s) ]
Maintenance [2 Certification Exam(s) ]
McAfee [8 Certification Exam(s) ]
McData [3 Certification Exam(s) ]
Medical [69 Certification Exam(s) ]
Microsoft [375 Certification Exam(s) ]
Mile2 [3 Certification Exam(s) ]
Military [1 Certification Exam(s) ]
Misc [1 Certification Exam(s) ]
Motorola [7 Certification Exam(s) ]
mySQL [4 Certification Exam(s) ]
NBSTSA [1 Certification Exam(s) ]
NCEES [2 Certification Exam(s) ]
NCIDQ [1 Certification Exam(s) ]
NCLEX [2 Certification Exam(s) ]
Network-General [12 Certification Exam(s) ]
NetworkAppliance [39 Certification Exam(s) ]
NI [1 Certification Exam(s) ]
NIELIT [1 Certification Exam(s) ]
Nokia [6 Certification Exam(s) ]
Nortel [130 Certification Exam(s) ]
Novell [37 Certification Exam(s) ]
OMG [10 Certification Exam(s) ]
Oracle [282 Certification Exam(s) ]
P&C [2 Certification Exam(s) ]
Palo-Alto [4 Certification Exam(s) ]
PARCC [1 Certification Exam(s) ]
PayPal [1 Certification Exam(s) ]
Pegasystems [12 Certification Exam(s) ]
PEOPLECERT [4 Certification Exam(s) ]
PMI [15 Certification Exam(s) ]
Polycom [2 Certification Exam(s) ]
PostgreSQL-CE [1 Certification Exam(s) ]
Prince2 [6 Certification Exam(s) ]
PRMIA [1 Certification Exam(s) ]
PsychCorp [1 Certification Exam(s) ]
PTCB [2 Certification Exam(s) ]
QAI [1 Certification Exam(s) ]
QlikView [1 Certification Exam(s) ]
Quality-Assurance [7 Certification Exam(s) ]
RACC [1 Certification Exam(s) ]
Real-Estate [1 Certification Exam(s) ]
RedHat [8 Certification Exam(s) ]
RES [5 Certification Exam(s) ]
Riverbed [8 Certification Exam(s) ]
RSA [15 Certification Exam(s) ]
Sair [8 Certification Exam(s) ]
Salesforce [5 Certification Exam(s) ]
SANS [1 Certification Exam(s) ]
SAP [98 Certification Exam(s) ]
SASInstitute [15 Certification Exam(s) ]
SAT [1 Certification Exam(s) ]
SCO [10 Certification Exam(s) ]
SCP [6 Certification Exam(s) ]
SDI [3 Certification Exam(s) ]
See-Beyond [1 Certification Exam(s) ]
Siemens [1 Certification Exam(s) ]
Snia [7 Certification Exam(s) ]
SOA [15 Certification Exam(s) ]
Social-Work-Board [4 Certification Exam(s) ]
SpringSource [1 Certification Exam(s) ]
SUN [63 Certification Exam(s) ]
SUSE [1 Certification Exam(s) ]
Sybase [17 Certification Exam(s) ]
Symantec [135 Certification Exam(s) ]
Teacher-Certification [4 Certification Exam(s) ]
The-Open-Group [8 Certification Exam(s) ]
TIA [3 Certification Exam(s) ]
Tibco [18 Certification Exam(s) ]
Trainers [3 Certification Exam(s) ]
Trend [1 Certification Exam(s) ]
TruSecure [1 Certification Exam(s) ]
USMLE [1 Certification Exam(s) ]
VCE [6 Certification Exam(s) ]
Veeam [2 Certification Exam(s) ]
Veritas [33 Certification Exam(s) ]
Vmware [58 Certification Exam(s) ]
Wonderlic [2 Certification Exam(s) ]
Worldatwork [2 Certification Exam(s) ]
XML-Master [3 Certification Exam(s) ]
Zend [6 Certification Exam(s) ]
References :
Killexams 156-727-77 exams | Killexams 156-727-77 cert | Pass4Sure 156-727-77 questions | Pass4sure 156-727-77 | pass-guaratee 156-727-77 | best 156-727-77 test preparation | best 156-727-77 training guides | 156-727-77 examcollection | killexams | killexams 156-727-77 review | killexams 156-727-77 legit | kill 156-727-77 example | kill 156-727-77 example journalism | kill exams 156-727-77 reviews | kill exam ripoff report | review 156-727-77 | review 156-727-77 quizlet | review 156-727-77 login | review 156-727-77 archives | review 156-727-77 sheet |legitimate 156-727-77 | legit 156-727-77 | legitimacy 156-727-77 | legitimation 156-727-77 | legit 156-727-77 check | legitimate 156-727-77 program | legitimize 156-727-77 | legitimate 156-727-77 business | legitimate 156-727-77 definition | legit 156-727-77 site | legit online banking | legit 156-727-77 website | legitimacy 156-727-77 definition | >pass 4 sure | pass for sure | p4s |pass4sure certification | pass4sure exam | IT certification | IT Exam | 156-727-77 material provider | pass4sure login | pass4sure 156-727-77 exams | pass4sure 156-727-77 reviews | pass4sure aws| pass4sure 156-727-77 security | pass4sure cisco | pass4sure coupon | pass4sure 156-727-77 dumps | pass4sure cissp | pass4sure 156-727-77 braindumps | pass4sure 156-727-77 test | pass4sure 156-727-77 torrent | pass4sure 156-727-77 download | pass4surekey | pass4sure cap | pass4sure free | examsoft | examsoft login | exams | exams free | examsolutions | exams4pilots | examsoft download | exams questions | examslocal | exams practice |